In an earlier post I walked through a cool SSRF vulnerability related to the ES plugin affecting later versions of Adminer. In much older versions it used to be possible to perform port scans using the standard MySQL plugin - and best of all it required no extra effort, everything needed is in front of you.
After a standard scan of a target, I found adminer.php on the root of the domain but only on HTTP, not HTTPS - there had been what looked to be a misconfiguration on the server side as HTTP was serving different content to HTTPS.
Proving SSRF
I needed to first prove that I could determine an open port vs a closed port, and this was fairly easily achieved as the error is verbose when attempting a connection on a given port.
Open port:
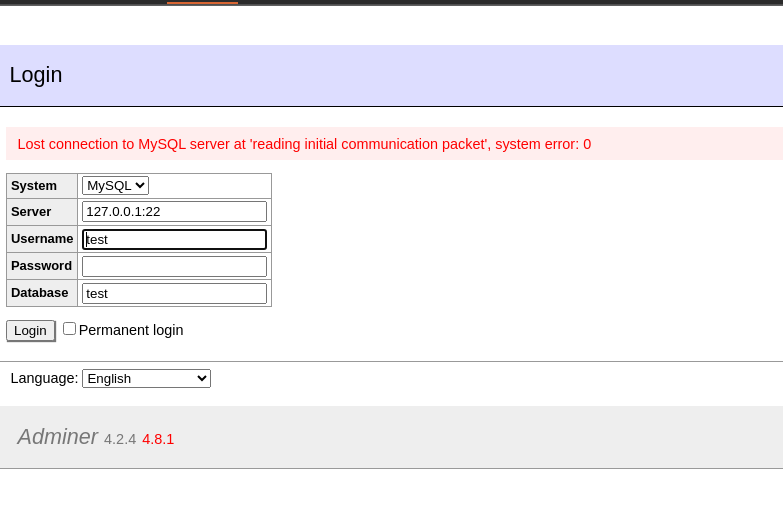
Closed port:
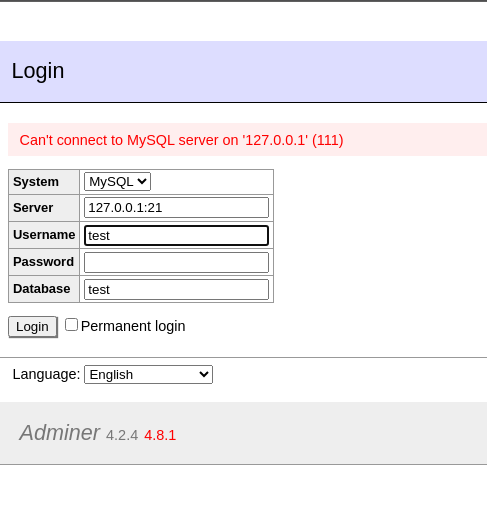
With some staggering of requests using Burp Intruder to avoid a backoff, I was able to determine open ports on the localhost - I had what I needed to raise a report.
Within a few hours of reporting, I had received a bounty:
Sometimes it is just that easy, and when your luck's in... your luck's in. Do the basics well, and it'll occasionally pay off!