.env files are interesting as they can often contain information should be kept away from the public. In some cases they can contain valid credentials for external facing services that can be accessed by a hacker, as was the case in this finding.
After doing some subdomain enumeration on one of my favorite targets, I'd found an interesting looking subdomain on the list that looked to be new. It was related to other functionality which I knew was normal for the domain but it had a strange word suffixed to the end so I went to take a look.
The site was empty, it was just showing a blank page... so I had to give it a quick scan, just in-case! Behind the scenes I had identified it was running Laravel, so I tweaked my scanning a little and managed to identify .env on the root of the webserver, below shows the redacted output:
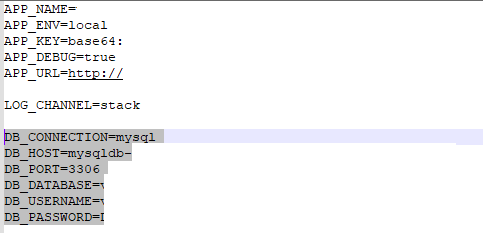
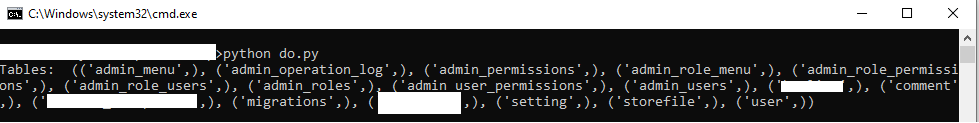
Inside the file was some credentials, and upon testing I could use these to connect to the remote database listed in the file as it was hosted in the cloud. I created the triage team a script to extract some common data to show what was possible, and below is a redacted output of what was seen:
After a few hours I had my report triaged and was paid out, one of the best parts of bug bounty!
In bug bounty, it's rarely a skill issue if you're finding duplicates, it's often the case of being at the right place at the right time for common issues like this. If you're finding duplicates, you're following the steps of someone who got paid and you're on the right path. I am confident if I was a day later someone else would've found the subdomain and found this too – I got very lucky!
Developers get it wrong sometimes as shown here, and that's one of the great benefits of PTaaS and bug bounty. Often serious issues are picked up by the good guys before any damage is done.